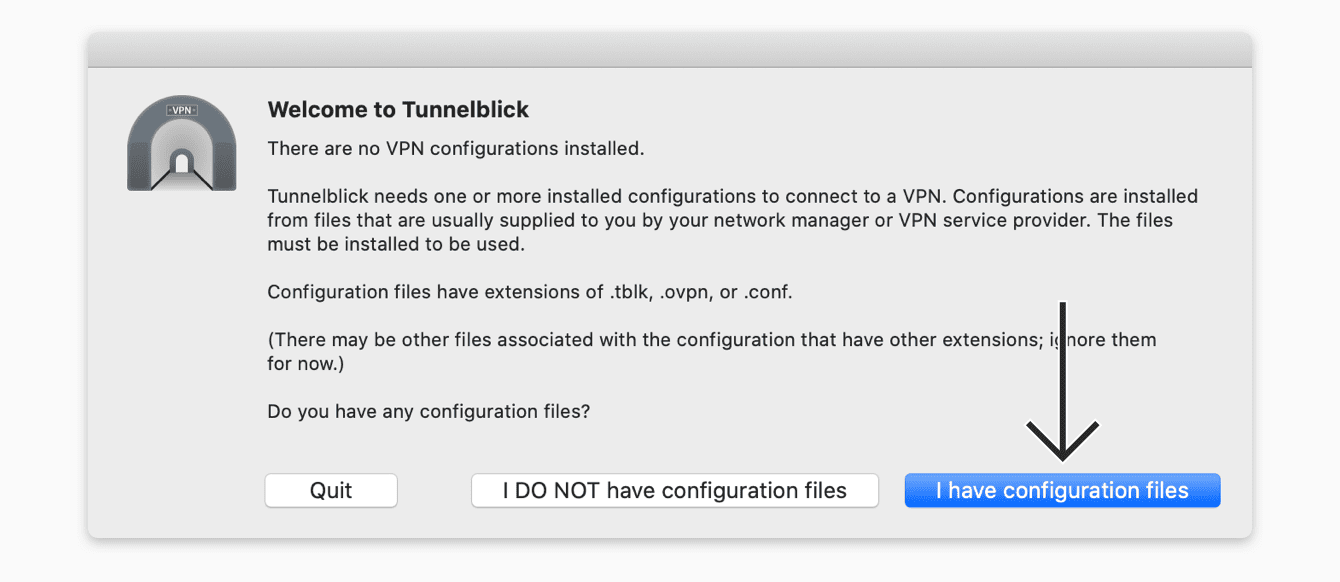
Configure SSL VPN with Tunnel Access Mode in Cyberoam. To know how to configure SSL VPN in. Use a VPN app that implements split tunneling. Several (not many) VPN services implement VPN. Start tunnelblick from your applications folder in finder, you should see a new icon at the top right side of your screen. Click on the icon and choose 'Connect AzireVPN'. Enter your credentials you use when you login to the AzireVPN site. You tunnel should now become yellow if you are successfully connected. On your Mac, choose Apple menu System Preferences, click Sharing, then select Internet Sharing in the service list. Open Sharing preferences for me. Click the “Share your connection from” pop-up menu, then choose the internet connection you want to share. For example, if you’re connected to the internet over Ethernet, choose Ethernet.
Highlighted Articles Discussion Group | On This Page Troubleshooting this problem could be very simple: try connecting the VPN with and without 'Set nameserver' selected. If one way or the other solves your problem, you're done! OpenVPN is such a powerful tool with so many options, and computer configurations are so varied, that it is impossible to have an exhaustive troubleshooting guide. This guide is meant for the most common setups, so if it doesn't apply to your situation, or doesn't help, see the Support page for guidance. This page assumes that you are successfully connected to a VPN server. If not, or if you aren't sure, look at Common Problems. If OpenVPN is connected to the server but you can't access the InternetAfter connecting, if you can't reach the Internet, it's likely that your setup has
Tunnelblick includes the ability to diagnose some DNS problems and will warn you about some common configuration problems. Check for a DNS problem: If you don't have a DNS problem then there is something else going on. See the Support page for guidance. If you have a DNS problem:
How to check your DNS settings
Note: If the DNS server list is dimmed (grayed out), it was set via DHCP, not manually. How to use a different DNS serverThere are two ways to set up a different DNS server: Use a different DNS server whether or not a VPN is activeYou can set your computer up to use a different DNS server all the time. Google Public DNS is free, and OpenDNS has a free version. There are lots of others. To use such a DNS server all the time (whether or not a VPN is connected):
This will set up your computer to always (whether or not you are connected to the VPN) use two Google DNS servers and two OpenDNS servers (in that order). Substitute the addresses for the DNS provider of your choice if you want. Use a different DNS server only when the VPN is activeNote: This will only work if you specify 'Set nameserver' in Tunnelblick's settings for the configuration. Add a line to your OpenVPN configuration file for each DNS server: ' If OpenVPN is connected to the server but your IP address does not changeIf you have a check in the 'Check if the apparent public IP address changed after connecting' checkbox on the 'Settings' tab of Tunnelblick's 'VPN Details' window, and your IP address doesn't change after connecting, a window will pop up to notify you. If OpenVPN connects to the server properly but your IP address does not change, your OpenVPN setup needs to include the '--redirect-gateway' option. By default, OpenVPN only sends some traffic through the VPN — traffic that is specifically destined for the VPN network itself. The '--redirect-gateway' option tells OpenVPN to send all IPv4 traffic through the VPN. There are three ways the option can be added; you need only use one:
(The '--' at the start of an OpenVPN option is omitted when the option appears in a configuration file.) How to test your IP addressYou can find out what IP address your computer is using by going to https://tunnelblick.net/ipinfo. The first number shown is your apparent public IP address: Note: tunnelblick.net does not use Javascript, other client-side scripting, plugins, trackers, beacons, or web bugs, and it does not carry advertising. It does not store cookies or any other data on your computer (except as noted in the tunnelblick.net privacy policy). If you have checked 'Check if the apparent public IP address changed after connecting', the IP address will be displayed in the Tunnelblick menu while you are connected: |
2014-04-11 10:18:57 *Tunnelblick: OS X 10.9.2; Tunnelblick 3.4beta22 (build 3789); prior version 3.4beta20 (build 3727)
2014-04-11 10:18:57 *Tunnelblick: Attempting connection with Diskstation using shadow copy; Set nameserver = 1; monitoring connection
2014-04-11 10:18:57 *Tunnelblick: openvpnstart start Diskstation.tblk 1337 1 0 1 0 305 -ptADGNWradsgnw 2.2.1
2014-04-11 10:18:58 *Tunnelblick: openvpnstart log:
Loading tun-signed.kext
OpenVPN started successfully. Command used to start OpenVPN (one argument per displayed line):
/Applications/Tunnelblick.app/Contents/Resources/openvpn/openvpn-2.2.1/openvpn
--daemon
--log
/Library/Application Support/Tunnelblick/Logs/-SUsers-STimo-SLibrary-SApplication Support-STunnelblick-SConfigurations-SDiskstation.tblk-SContents-SResources-Sconfig.ovpn.1_0_1_0_305.1337.openvpn.log
--cd
/Library/Application Support/Tunnelblick/Users/Timo/Diskstation.tblk/Contents/Resources
--config
/Library/Application Support/Tunnelblick/Users/Timo/Diskstation.tblk/Contents/Resources/config.ovpn
--cd
/Library/Application Support/Tunnelblick/Users/Timo/Diskstation.tblk/Contents/Resources
--management
127.0.0.1
1337
--management-query-passwords
--management-hold
--script-security
2
--up
/Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -m -w -d -f -ptADGNWradsgnw
Share Tunnelblick Connection Mac Free
--down
/Applications/Tunnelblick.app/Contents/Resources/client.down.tunnelblick.sh -m -w -d -f -ptADGNWradsgnw
2014-04-11 10:18:57 OpenVPN 2.2.1 i386-apple-darwin10.8.0 [SSL] [LZO2] [PKCS11] [eurephia] built on Apr 8 2014
2014-04-11 10:18:57 *Tunnelblick: openvpnstart starting OpenVPN
2014-04-11 10:18:58 *Tunnelblick: Established communication with OpenVPN
2014-04-11 10:19:08 IMPORTANT: OpenVPN's default port number is now 1194, based on an official port number assignment by IANA. OpenVPN 2.0-beta16 and earlier used 5000 as the default port.
2014-04-11 10:19:08 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
2014-04-11 10:19:08 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
2014-04-11 10:19:08 LZO compression initialized
2014-04-11 10:19:08 UDPv4 link local (bound): [undef]:1194
2014-04-11 10:19:08 UDPv4 link remote: xxx.xxx.xxx.xxx:1194
2014-04-11 10:19:08 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2014-04-11 10:19:08 [synology.com] Peer Connection Initiated with xxx.xxx.xxx.xxx:1194
2014-04-11 10:19:11 TUN/TAP device /dev/tun0 opened
2014-04-11 10:19:11 /sbin/ifconfig tun0 delete
ifconfig: ioctl (SIOCDIFADDR): Can't assign requested address
2014-04-11 10:19:11 NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2014-04-11 10:19:11 /sbin/ifconfig tun0 10.8.0.6 10.8.0.5 mtu 1500 netmask 255.255.255.255 up
2014-04-11 10:19:11 /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -m -w -d -f -ptADGNWradsgnw tun0 1500 1542 10.8.0.6 10.8.0.5 init
**********************************************
Start of output from client.up.tunnelblick.sh
Retrieved from OpenVPN: name server(s) [ 192.168.200.1 ], search domain(s) [ ] and SMB server(s) [ ] and using default domain name [ openvpn ]
Not aggregating ServerAddresses because running on OS X 10.6 or higher
Setting search domains to 'openvpn' because running under OS X 10.6 or higher and the search domains were not set manually and 'Prepend domain name to search domains' was not selected
Saved the DNS and SMB configurations so they can be restored
Set ServerAddresses to 192.168.200.1
Set SearchDomains to openvpn
Tunnelblick App
Set DomainName to openvpn
Flushed the DNS Cache
Setting up to monitor system configuration with process-network-changes
End of output from client.up.tunnelblick.sh
**********************************************
add net xx.x..xx.xx: gateway xx.xx.xx.xx
delete net 0.0.0.0: gateway xx.xx.xx.xx
add net 0.0.0.0: gateway 10.8.0.5
add net 192.168.200.0: gateway 10.8.0.5
2014-04-11 10:19:14 *Tunnelblick: No 'connected.sh' script to execute
2014-04-11 10:19:14 WARNING: potential route subnet conflict between local LAN [10.8.0.0/255.255.255.0] and remote VPN [10.8.0.0/255.255.255.0]
add net 10.8.0.0: gateway 10.8.0.5
2014-04-11 10:19:14 WARNING: potential route subnet conflict between local LAN [10.8.0.0/255.255.255.0] and remote VPN [10.8.0.1/255.255.255.255]
add net 10.8.0.1: gateway 10.8.0.5
2014-04-11 10:19:14 Initialization Sequence Completed
2014-04-11 10:19:19 *Tunnelblick process-network-changes: A system configuration change was ignored
2014-04-11 10:19:20 *Tunnelblick: This computer's apparent public IP address changed from xx.xx.xx.xx before connection to xx.xx.xx.xx after connection
Console Log:
2014-04-11 10:04:06 Tunnelblick[205] Set program update feedURL to https://www.tunnelblick.net/appcast-b.rss
Non-Apple kexts that are loaded:
Index Refs Address Size Wired Name (Version) <Linked Against>
Share Tunnelblick Connection Mac Free
126 0 0xffffff7f8209d000 0x6000 0x6000 net.tunnelblick.tun (1.0) <7 5 4 1>
